
shellcode란, 취약한 프로그램에 대하여 공격자가 실행시키고자 하는 코드임다.
흔히 쉘(shell)을 실행시키기 떄문에 shellcode라는 이름이 붙었지요.
상황에따라 사용되는 쉘코드의 종류는 굉장히 다양한데,
매번 우리가 원하는 쉘코드를 구글링해서 붙여쓸수는 없겠죠?
그래서 이번 기회에 쉘코드 제작에 관한 전반적인 과정들을 같이 알아볼까 합니다.
첫 코딩 국룰, "세상에게 인사하기"
우선, 이번시간에는 c언어 프로그램의 함수 호출과정을 분석해보기까지 해봅시다.
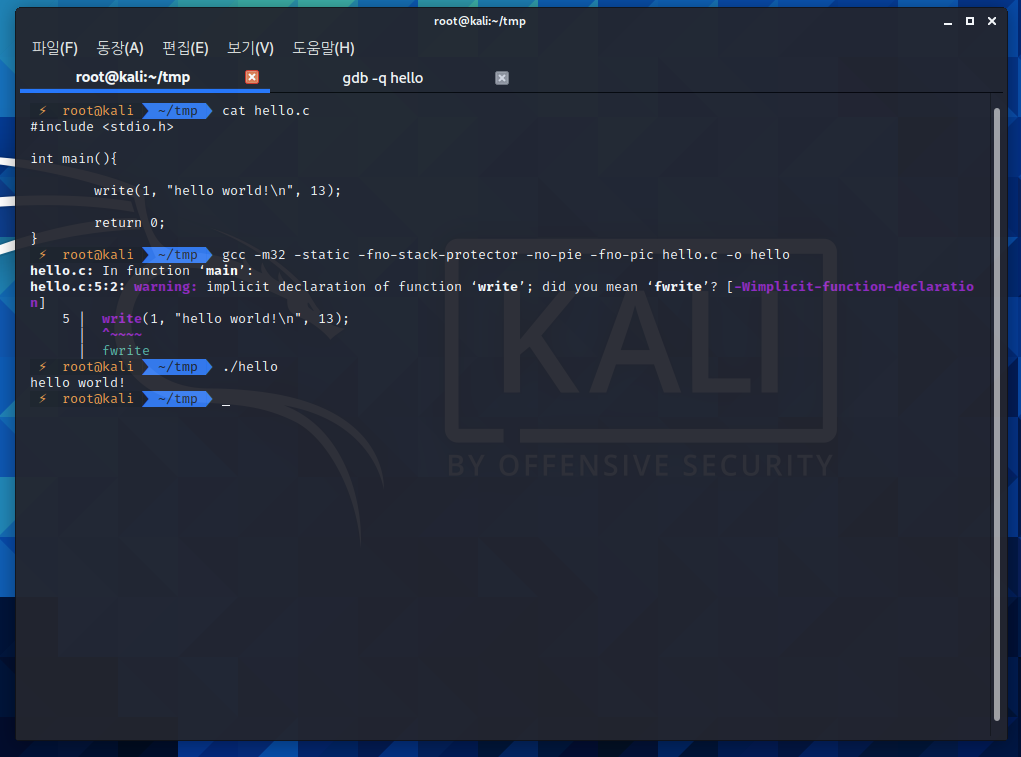
깔끔하게 분석하고자 보호기법들을 대강 꺼주었습니다.
-fno-stack-protector
-no-pie
-fno-pic
글고 정적 할당과 32bit 컴파일 옵션
-static
-m32
각 보호기법들의 세세한 작동 과정은 따로 포스팅 해 놓겠슴다.
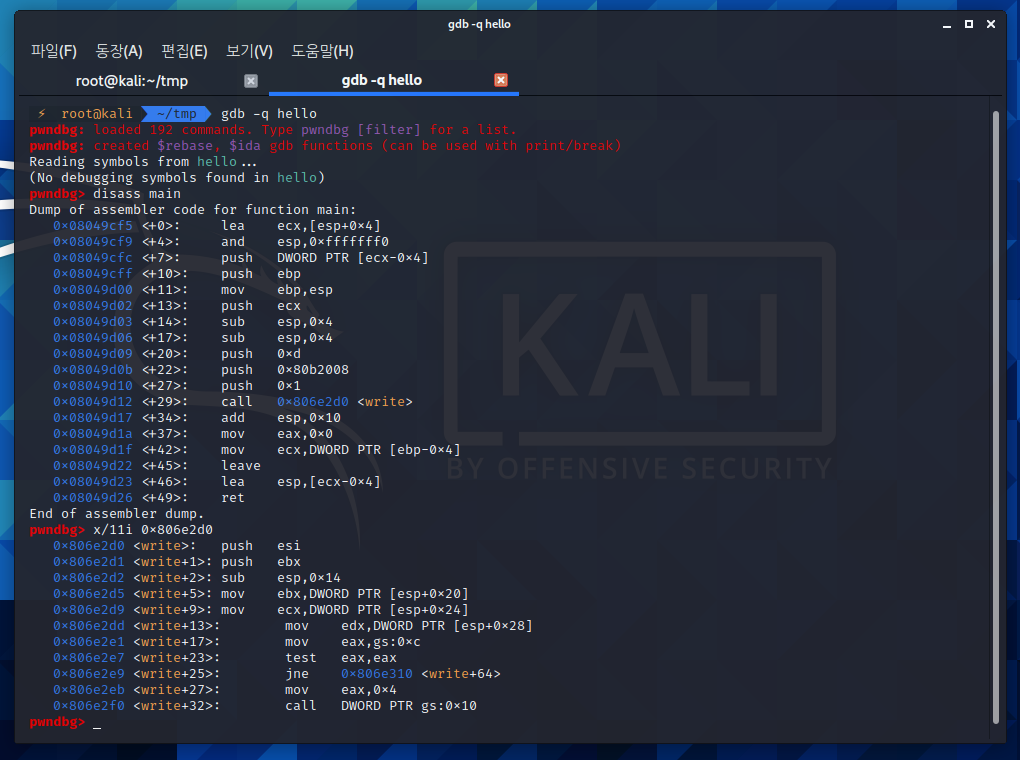
우리가 여기서 집중 분석해 볼 곳은 system call 까지의 부분 입니다.
main + 29의 wirte 함수는 호환성, 편리성을 위한 c언어 라이브러리 함수이고,
해당 코드 속으로 들어가보면 kernal mode로 진입하는 부분
즉, system call을 호출하는 부분이 있답니다.
바로 call dword ptr gs:0x10 <write + 32>
glibc-2.16.0/sysdeps/unix/sysv/linux/i386/sysdep.h:
/* The original calling convention for system calls on Linux/i386 is
to use int $0x80. */
#ifdef I386_USE_SYSENTER
# ifdef SHARED
# define ENTER_KERNEL call *%gs:SYSINFO_OFFSET
# else
# define ENTER_KERNEL call *_dl_sysinfo
# endif
#else
# define ENTER_KERNEL int $0x80
#endif
sysenter 방식에 관한 자세한 자세한 설명은 이곳을 참고하시길 바라겠습니다.
https://stackoverflow.com/questions/34741378/confusion-with-system-call
Confusion with system call
I am trying to understand how a system call is made in x86. I am reading Smashing the stack for fun and profit. There is a function given on page 7: #include void main() { char...
stackoverflow.com
system call 호출 전, 인자들을 어떠한 방식으로 전달할까요?
직전에 break point를 걸고 레지스터의 상태를 확인해봅시다.
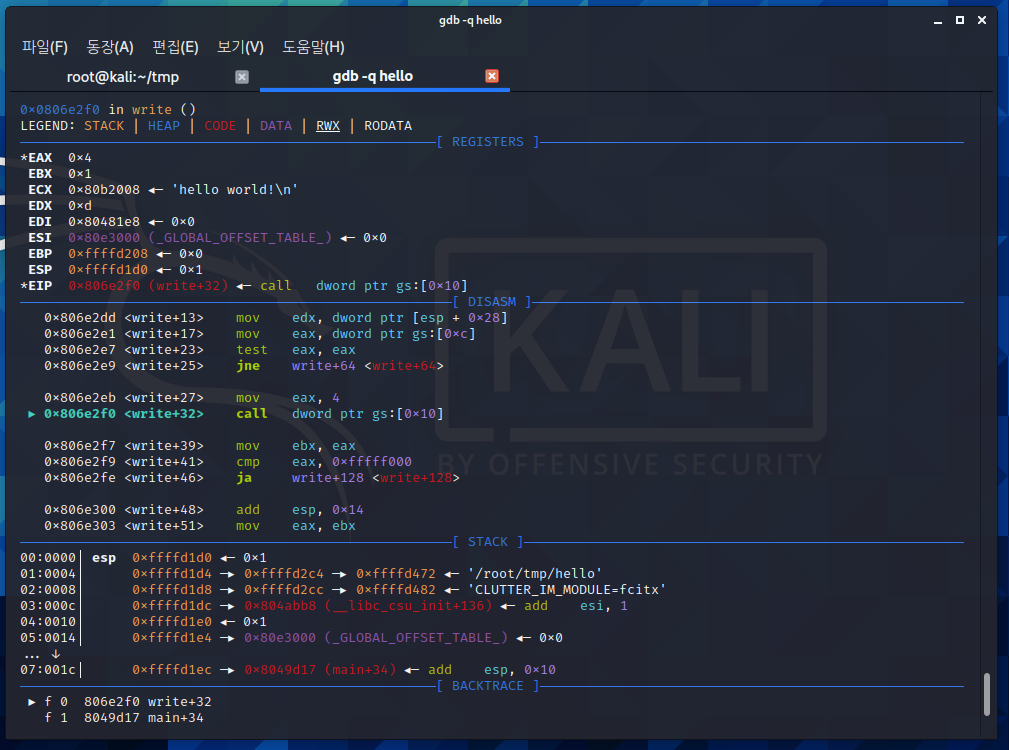
아래 링크속 syscall reference 대로, 다음과같이 인자를 넘겨주는 모습입니다.
| eax | ebx | ecx | edx |
| 0x4 | 0x1 | 'hello world'의 주소 | 0xd |
eds000n.github.io/syscalls-x86.html
Linux Syscall Reference
eds000n.github.io
eax : system call 번호 (4 → write)
ebx : fd (1 → stdout)
ecx : *buf
edx : count (0xd → 문자열의 길이)
그렇다면 이 부분만 따로 어셈블리어로 만든다면?
to be continued..
'system hacking 📱 > shellocde' 카테고리의 다른 글
| shellcode (0x2f 없애기) (0) | 2020.12.19 |
|---|---|
| shellcode (4) (0) | 2020.12.19 |
| shellcode (3) (0) | 2020.12.18 |
| shellcode (2) (0) | 2020.12.18 |