
1편에 이어서 system call 호출 부분만을 따로 shellcode를 만들어봅시다.

저는 개인적으로 더 편한 intel 문법으로 코딩해 볼게요.
| hello.asm | → | hello.o | → | hello |
| assembly source file | assembler (nasm) | object file | linker (ld) | executable file |
<hello.asm>
1 BITS 32
2
3 global _start
4
5 section .text
6 _start:
7 ; write(4, "hello world!" addr, 13)
8 mov eax, 4
9 mov ebx, 1
10 push 0x0a
11 push 0x21646c72
12 push 0x6f77206f
13 push 0x6c6c6568
14 mov ecx, esp
15 mov edx, 13
16 int 0x80
17
18 ; exit(0)
19 mov eax, 1
20 mov ebx, 0
21 int 0x80
BITS 32 : 32bit 프로그램 임을 명시
global _start : Linker 로 하여금 실행 파일을 만들때 _start 함수가 entry point 임을 명시
section .text : text섹션에 다음을 입력
mov {destination}, {source} : 후자의 값을 전자에 복사
push {data} : stack에 data를 저장
int 0x80 : system call 호출
eds000n.github.io/syscalls-x86.html
Linux Syscall Reference
eds000n.github.io
system call write 함수는 총 4개의 레지스터를 사용합니다.
| eax | ebx | ecx | edx |
| write함수의 syscall 번호 | fd (파일 디스크립터) | *buf (문자열의 주소) | len (문자열의 길이) |
| 4 | 1 | &(문자열) | 13 |
여기서 ecx에 어떻게 문자열의 주소를 넣는지 봅시다. (코드10~14)
- push를 통해 "hello world!\n"를 스택상에 올리기
- mov ecx, esp를 통해 ecx에 해당스택의 주소를 복사
1번 과정을 통해 stack에는 "hello world!\n"문자열이 올라가게 되고, esp는 이를 가리키게 됩니다.
(esp레지스터는 스택 끝부분의 주소를 담고있습니다.)
=====================================
= "hello world\n" → 0x68656c6c6f20776f726c64210a
= little endian 방식으로 4byte씩 끊어서 push합니다.
=
= ← push
= 0x68656c6c | 0x6f20776f | 0x726c6421 | 0x0000000a
= 왜그런건지는 다들 아실거라 생각합니다.
======================================
이렇게 stack의 주소가 담긴 esp를 ecx에 넣어줌 으로써, 문자열의 주소가 들어가게 됩니다.
마찬가지로 프로그램의 정상적인 종료를 위해 exit 함수를 실행시킵니다.
| eax | ebx |
| exit 함수의 syscall 번호 | error_code |
| 1 | 0 |
만들어진 프로그램을 실행시켜보면 반갑게 세상에게 인사합니다.
이제 objdump를 이용하여 기계어코드를 쭉 뽑아낼 차례 (고것이 바로 shellcode)

저는 간단한 python 프로그램을 만들어봤는데 관련 모듈이 있는지 찾아봐야겠네요..^^;;
상당히 무식하게 만들어놔서 부끄럽지만, 혹시 사용하실분 계시다면.. 감히 올려보겠습니다.
import os
os.system("objdump -d hello > temp")
f = open('temp', 'r')
shellcode = ""
data = f.read().split('\n\n')
for i in range(2, len(data)):
tmp = data[i].split('\t')
tmp2 = ""
for j in range(len(tmp)/2):
tmp2 = tmp[j*2+1]
tmp2 = tmp2.split(' ')
code = ""
for k in range(len(tmp2)):
code += tmp2[k]
for k in range(len(code)/2):
shellcode += "\\x" + code[k*2:k*2+2]
os.system("rm temp")
print "shellcode len : " + str(len(shellcode)/4)
print shellcode
3번째 줄 objdump -d {파일명}을 적절히 변경하여 python2 로 실행시켜 보면
아마 요로케 잘 나올겁니다.
shellcode len : 48
\xb8\x04\x00\x00\x00\xbb\x01\x00\x00\x00\x6a\x0a\x68\x72\x6c\x64\x21\x68\x6f\x20\x77\x6f\x68\x68\x65\x6c\x6c\x89\xe1\xba\x0d\x00\x00\x00\xcd\x80\xb8\x01\x00\x00\x00\xbb\x00\x00\x00\x00\xcd\x80
첫 shellcode를 만들어봤습니다
이제 직접 한번 사용해보러 가보죠
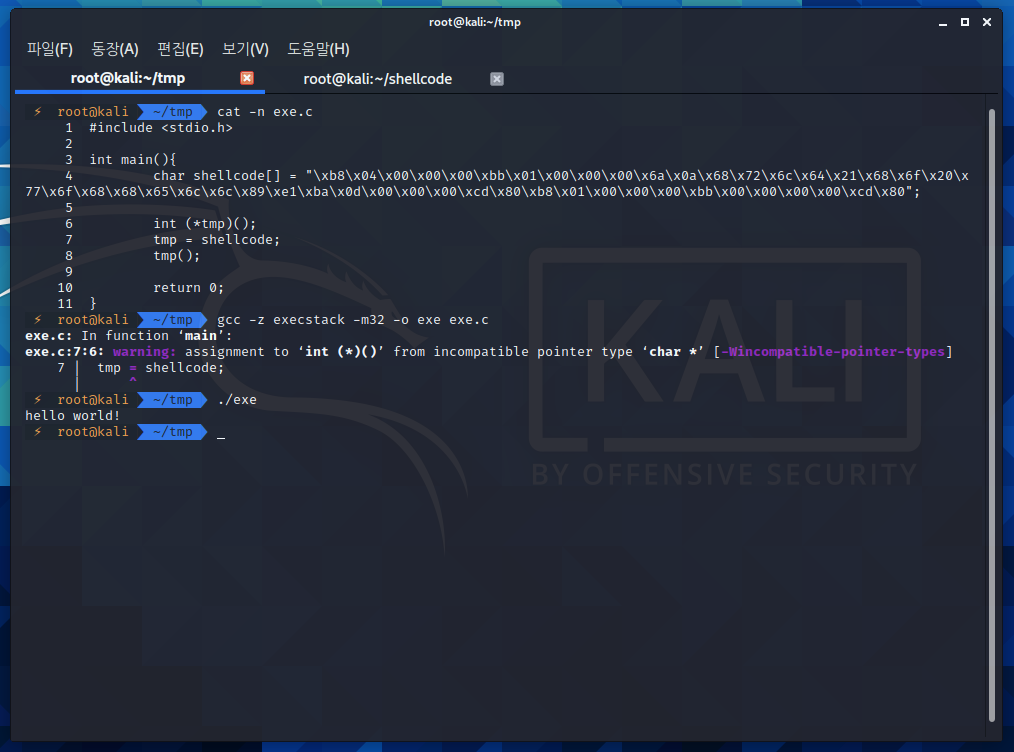
변수 shellcode에 각자 만든 shellcode를 넣어주시고
컴파일을 거친 프로그램을 실행시키면 성공적으로 hello world!
여기서 주의해야할 점은 gcc 컴파일 옵션에 -z execstack 옵션을 꼭 넣어주셔야 합니다.
변수 shellcode가 stack상에 올라가 있기 때문에 해당 옵션이 없다면 보호기법에 의해 실행이 되지 않습니다.

GNU_STACK의 플래그를 잘 보면 보호기법을 꺼주었을때 E(실행권한)가 추가 되었음을 볼수 있죠?
이렇게 성공적으로 shellcode를 만들어보았습니다... 라고 할줄 알았다면 경기도 오산.
만든 shellcode를 실제 공격에 한번 사용해 보시면 아마 작동이 되질 않을겁니다.
그 이유는 shellcode속 0x00때문인데요.
다들 아시다시피 0x00을 만나면 프로그램이 문자열의 끝으로 간주하기 때문에 뒤 코드가 무시됩니다.
한번 볼까요
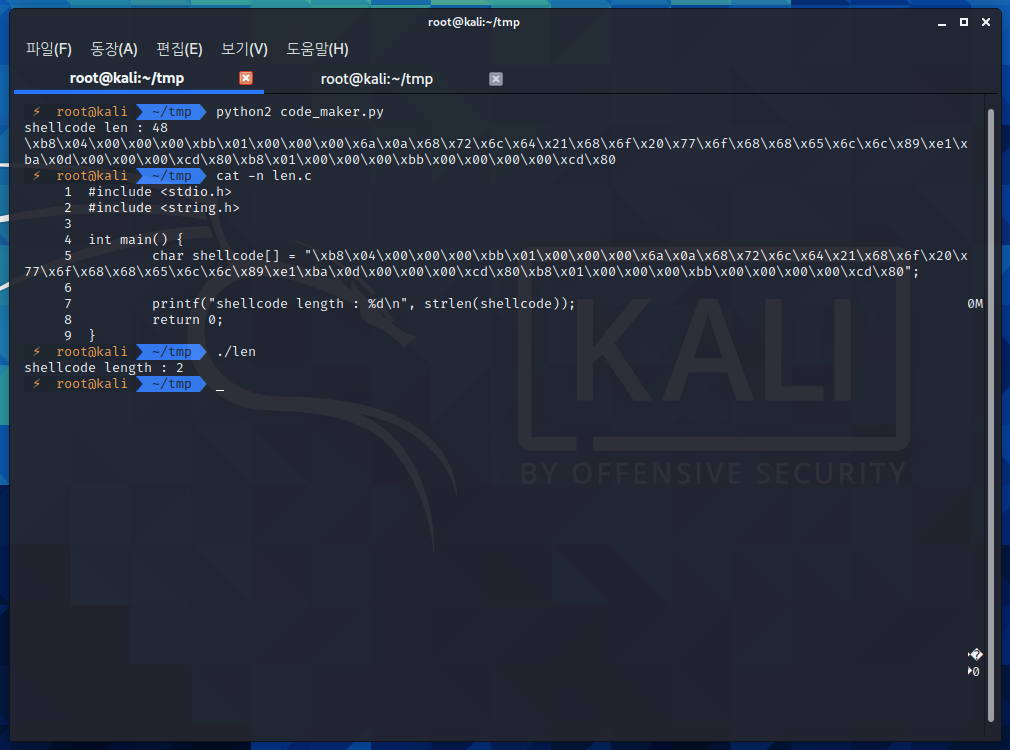
길이가 48이 아닌, 2라고 나오죠?
이를 우짤고...
to be continued..
'system hacking 📱 > shellocde' 카테고리의 다른 글
| shellcode (0x2f 없애기) (0) | 2020.12.19 |
|---|---|
| shellcode (4) (0) | 2020.12.19 |
| shellcode (3) (0) | 2020.12.18 |
| shellcode (1) (0) | 2020.12.17 |